I just got an email forwarded to me from another employee within my company (she doesn’t work in IT). This is a scam that’s been around a long time…first via regular snail mail, and now via email. The problem, though, is it still works and it’s very easy to do. Just send a bunch of letters and emails to as many people as possible, stating that their domain names are expiring, and just send a check (or visit a website) to renew. Take a look at this…
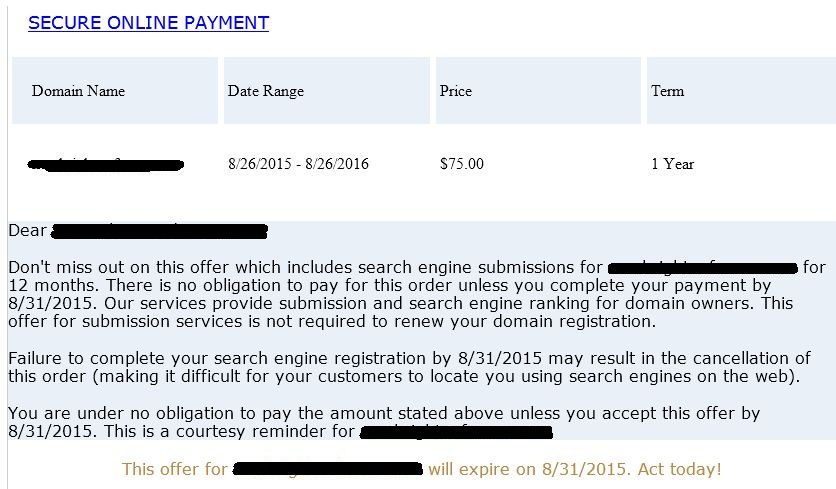
Yes, the wording is simplistic, but it does look nice, and the cost is rather insignificant compared to all the other day-to-day invoices that crosses a employees desk. And you know what? A lot of people just pay this, without even thinking about it.
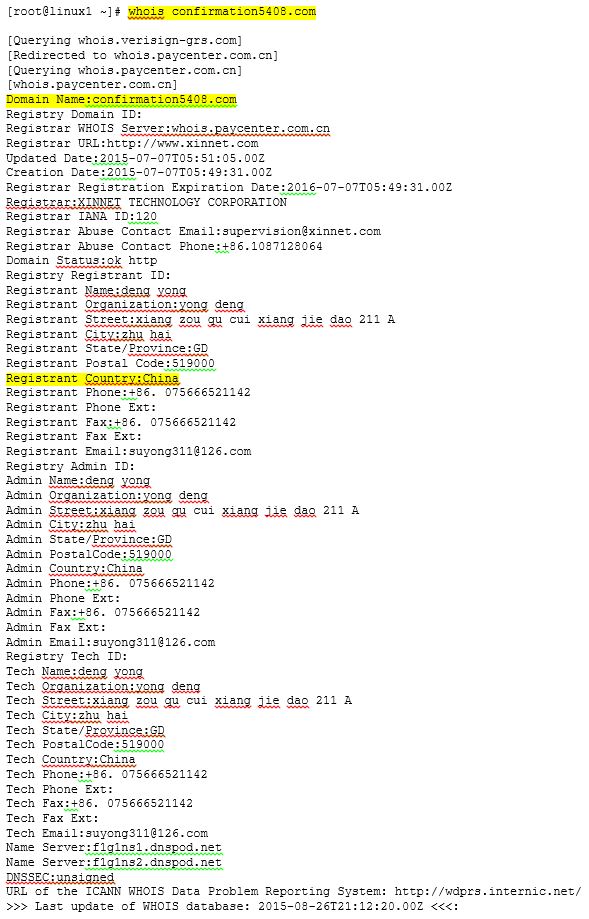
As for the link to make the payment, it points to the domain: confirmation5408.com
A simple whois shows that this is located in China, and the domain was just registered in early July. (Yeah, I know…I’m so shocked that this is located in China!!)
So…what to do? Ignore these letters and emails, and make sure that your employees forward any IT related invoices to you for approval. Lots of companies fall prey to this, but with your diligence your company won’t be one of them.