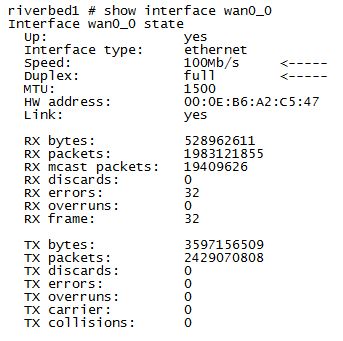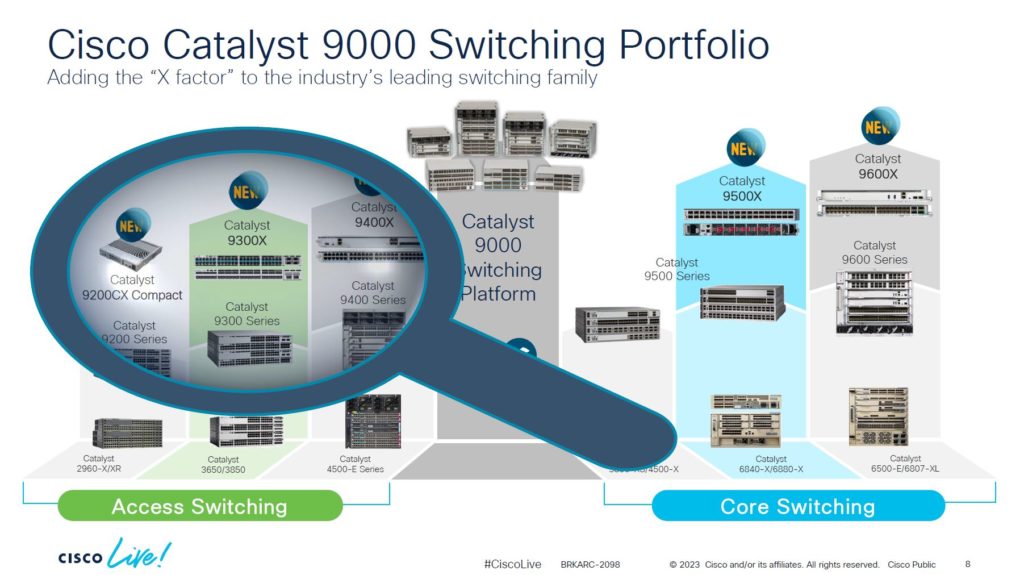
Had some good classes today!! I enjoyed the class that covered an overview of the CAT 9000 series of switches! Although the class was focused on the access layer, there was some info on the entire line. It’s nice to see that their various lines of switches (2900, 3600, 4500, and 6500) have all been consolidated into a single series of switches with a common architecture and operating system. With the 9000 series, it can take you from the access layer, through the distribution layer, and into the core. Thanks Cisco!!

I then took an intro class into BGP…it’s been a long time since I worked with BGP (it was still a 2-byte AS field). The two instructors, Gustavo Sibaja and Peter Paluch, did a very good job tackling a complex subject…and they made it fun!!
I also stopped by a variety of Cisco booths, checking in on the status of Cisco SIG, future plans for branch site security controls, etc. I can tell you this…Cisco is betting big with Secure Access! Umbrella SIG will ultimately be rolled into this service, and if Cisco can deliver on their promises, this could be a game changer for many organizations. Hopefully, it won’t have the growing pains that SIG had.
While walking around the World of Solutions, I noticed the Social Media Hub…

Other than taking this picture, you will never find me sitting in one of these! I am not a big believer in social media…in fact, I like to call it Anti-Social Media. There is a lot of potential good with social media…however, the results thus far have been largely negative, and even damaging. One can always hope…
Y’all have a great day!!
wri mem