First up…a quick apology. Back on April 10th, I posted Verifying Proper Email Routing – MX Records. At the end of the post I mentioned I would talk about the trailing dot shown in the DNS records in my next post. Well, I basically forgot. Life just got too busy.
But before I do that, you really need to get DIG installed on your Windows PC (if you have Linux then you should already have DIG). So today, lets get DIG installed and tested…this is a great tool to have, and you will be surprised at how often you will use it.
The package we are going to install is BIND (Berkeley Internet Name Domain) from ISC (Internet Systems Consortium). ISC has been around for years, and most DNS servers on the Internet run BIND (whether Windows or Linux/UNIX based). Do the following…
- Go to https://www.isc.org/downloads/bind
- There is a lot of good info on this page concerning BIND and DNS…I would recommend reading this when you have a chance.
- Click on Download BIND button
- Expand the BIND menu
- Click on the Download button to the right of the GREEN “Current-Stable” status
- In the window that pops open, choose the correct version for your system…(click the appropriate blue box)
- Next, create a directory in your C: drive called “bind”, move the BIND ZIP file to that directory, then double-click on the ZIP file. Extract all of the files in the \bind directory.
Now, lets test. Open up a command prompt and change to the BIND directory, then type in “dig” and press enter. You should see something like this…(this example is showing DIG returning a list of the ROOT servers on the Internet)…
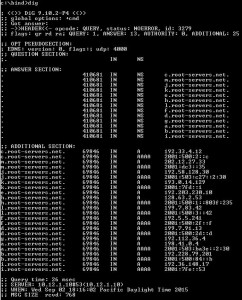
Running DIG at the command prompt
If it doesn’t work, there are a couple of common errors which are easily fixed…
32 bit installation error: You may get an error stating “The application has failed to start because its side-by-side configuration is incorrect”. If that’s the case, run the file “vcredist_x86.exe” which is located in the same “bind” directory. Then try running “dig” again…it should work.
64 bit installation error: If you get the error message stating that MSVCR110.DLL is missing, then do a search on the C: drive for that file, and copy it to the “bind” directory. Running “dig” should now work.
Now you can play with DIG…some examples…
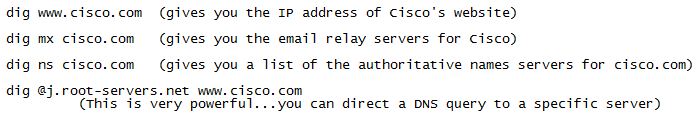
Some DIG examples
DIG is very powerful, and will quickly become your go-to tool when you have any DNS issues. I will talk more about using DIG in a future post.