So for the last couple of days, I’ve been in Nevada at one of our remote sites. (On a side note, the “middle of nowhere” pretty much describes all of Nevada!!) I was setting up a wireless bridge to connect separate parts of a large aggregate plant…it was a very busy few days. We kept running into problems, which took up a lot of time to resolve, but eventually we got things working. As I was testing the new subnet hanging off the bridge, I noticed that DHCP was not working…hmmm, very strange. I’ve configured DHCP many times over the years, and it just works. Time to troubleshoot…
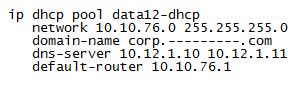
First test was easy…I configured a static IP on my laptop and everything worked great. Next I drove over to the other end which housed the main switch and router, and plugged into a port configured for the new VLAN….and no DHCP. Say what? Hmmm…I must have made a mistake on my configuration…but the DHCP pool looks good…
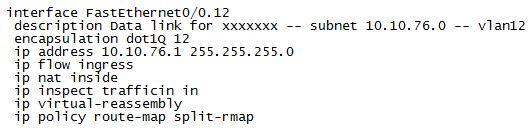
And the subinterface configuration looks good too…
Very interesting…the only thing left was the DCHP excluded-address config, but that’s so easy, I know that’s not the problem. But I checked it out anyways…
Say what?? How could I have messed that up? But I have to say, the configuration was doing exactly what I asked it to do…basically not handing out any IP’s!! So after a quick edit, everything was working properly…
So remember, most of the time, it will be the simple things that get you.