While researching some security stuff, I stumbled across the Peerlyst website…and wow!! This is a great resource for security professionals…lots of helpful information and discussions. Make sure you check out their list of security cheat sheets…this is a treasure trove of information all in one place!!
While researching some security stuff, I stumbled across the Peerlyst website…and wow!! This is a great resource for security professionals…lots of helpful information and discussions. Make sure you check out their list of security cheat sheets…this is a treasure trove of information all in one place!!
Memorial Day 2017 – Uncle Fred
I have been blessed with an incredible family…great parents and lots of wonderful Aunts and Uncles, all who were caring, funny, and supportive as far back as I can remember. One such person was my Uncle Fred. He always had time for me…for my questions and my inquisitive nature. As for the impact of a man upon my life, Uncle Fred was second only to my Dad.
I remember growing up as a kid and would spend time with Uncle Fred and Aunt Maude…they lived up in South Carolina, so it was a bit of a drive to get there from Georgia. He would show me and my brother around his property, and would especially linger in and around his shop. And what a shop it was! You see, Uncle Fred was a machinist (and maybe a Mechanical Engineer…not sure how accurate my memory is). And he NEVER threw anything away…never!
I remember one time when Uncle Fred was trying to explain to me how a differential worked. He made hand gestures and drawings on paper..but I still wasn’t getting it. He disappeared to his shop for a bit, and came back carrying a real differential…in his hands!! He then showed me how the gearing worked and the light bulb finally turned on!!
Uncle Fred was part of The Greatest Generation. He served in the Marines as part of the Seabees in World War II. The Seabees were USMC-trained soldiers who were also trained engineers and construction tradesmen. Talk about a one-two punch!! They could both fight and build…all in the same day if needed.
Another example Uncle Fred gave me was in marriage…he and my Aunt Maude were inseparable. They always held hands and joked with each other. They lived life to the fullest, trusted God, and were ready to help anyone in need.
Uncle Fred was 95 years old when he passed away a few weeks ago (on May 17th)…had he lived just one more week, he would have celebrated his 73 anniversary.
Thank you Uncle Fred for living a life that can be an example to us all. You will be missed always…
WannaCry Ransomware – That Got Our Attention, Didn’t It?
If you have not heard about the WannaCry ransomware that is (and perhaps was) running rampant over the past weekend, then you must have been in a cave or on your honeymoon! This one is a doozie, let me tell you!! Some quick facts…
- This ransomware is based on the EternalBlue exploit (developed by the NSA, and then stolen and leaked on the Internet)
- Microsoft released a patch for this (MS17-010) in March
- Some quick thinking good guys were able to slow down the spread of WannaCry by activating a killswitch within the ransomware code
- MANY people and organizations, throughout the world, have been hit by this
An excellent analysis of WannaCry can be found here…
WannaCry no more: ransomware worm IOC’s, Tor C2 and technical analysis + SIEM rules
Stay informed…AND patch your systems!!
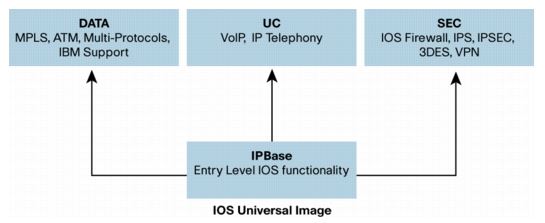
Cisco IOS Feature/License Options
I need to add a feature (or license) to a number of my Cisco routers. This can get a bit confusing though, as Cisco made changes to their licensing model when they introduced the ISR G2 series of routers (IE: 1900, 2900 & 3900 series).
These routers use a “universal” image, and you simply license the features you want…in my case the routers are licensed for IPBase and UC, and I need to add the SEC (Security) license to the router. The license tree is pretty simple…
For my older routers, I’m currently running SP Services and I need to add Security/VPN, which means I need to upgrade to Advanced IP Services.
Either way, Cisco is going to get a lot more money from me!!
SHA1 Got Shattered (Major Geek Stuff!!)
This blog is for us true geeks!! (All others will be bored.)
It was announced today that the cryptographic hash function SHA-1 is susceptible to collisions. Although this has been theorized for a number of years, there has been no proof of a collision. Well…until today, that is. Teams from CWI Amsterdam and Google have been working together for the last couple of years, and have demonstrated an actual collision.
What is a cryptographic collision? It’s when two different files have the same hash signature. In other words, if you run a hash function against a file, the resulting hash is a “signature” for that file. Change anything in that file, and the hash result will be very different. However, these teams were able to manipulate two different files and get the same hash signature. NOT good at all. The security implications for this is HUGE!
SHA-1 has already been deprecated, and is on it’s way out…today’s announcement adds urgency to it. You should move to SHA-256 or SHA-3.
For some really good reading on this, check out the following links…
At death’s door for years, widely used SHA1 function is now dead
Enjoy!!
SPARC and Solaris UNIX – A Sad Day Indeed
For those of you that have been involved in the IT industry for a long time, then you know the impact that Sun SPARC systems (and the Solaris operating system) has had on the industry and the Internet. It used to be that if you had an application that was critical or important, then it ran on UNIX and custom RISC processors, and that usually meant Sun hardware and software.
Early in my career, I managed several Sun systems that handled email, firewall (remember the early days of Checkpoint??), and critical databases….it was a lot of work, but the Sun platforms just rocked!! I remember hearing horror stories from other Admin’s about how buggy or poor performing their systems were (especially Windows NT Admin’s), and I just smiled…my SPARC systems and the Solaris OS never let me down!!
Back in 2010, Oracle bought Sun and tried to keep it going, but it’s not going to happen. I just saw this NetworkWorld article today…
Game Over for Solaris and SPARC?
One other memory…way back in my early days in this industry, I was working on the Smart Valley project (in the San Francisco Bay area)…this would have been in the mid-1990’s. I was handling the installation of Internet circuits and related equipment for the many schools in the Silicon Valley area, getting them hooked up to the “Internet”. I was green, and still had a lot to learn, but Sun assigned a number of their Network Engineers to the project and I remember how sharp and helpful they were. They showed a lot of patience to me, and I learned a lot…I am forever in their debt.
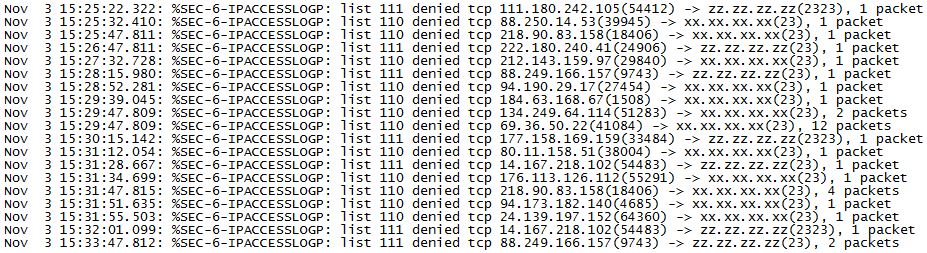
IoT (Internet-of-Things) and Port 23
Greetings…
Yes, I know…it has been a long time since my last post. Sorry…I’ve been busy.
This afternoon, I was doing some configuration work on one of my Internet facing routers, and I noticed a large amount of scanning, looking for an open Telnet port (scanning for ports 23 and 2323)…take a look…
I was wondering if it was just this router, so I checked several other routers on my network and they are all seeing exactly the same thing, and it all started at roughly the same time. VERY interesting! (Note…you may notice that there are two different ACL’s involved…that’s because I have two Internet facing ports…a primary circuit and a backup circuit, each with their own custom ACL.)
This activity might be related to the recent Mirai malware attacks on the “Internet of Things” (IoT), and the use of port 23 for C&C (Command & Control) traffic. Hard to say really…maybe it’s just ET trying to phone home…
Have a great day!!
CVD’s – Cisco Validated Design Guides
If you ever need some help in designing a network, wondering what’s the best practices for security or wireless, then Cisco has some very helpful information for you! Over the years, Cisco has put together a bunch of official network designs that you can review and use to assist with your own network design challenges. Cisco calls them CVD’s…or, Cisco Validated Designs. When they first started out, the designs were very technical and written in a bit of a bland manner (written by CCIE’s no doubt). Now, however, they are very colorful, lots of visuals and slick copy art, but…they are still technical and very helpful!! (I would imagine they are still written by a bunch of CCIE’s, but then filtered through a design/publishing group of some sort.)
Take a look at this link: Cisco Validated Designs
I’m in the process of reviewing and upgrading my core VTI/DMVPN infrastructure, and I’m reading through the CVD “Intelligent WAN Technology Design Guide”….
This design guide is NOT light reading…it’s 287 pages of very technical information and sample configurations…VERY cool. It’s going to take me several days to digest this thing…but already it has answered several questions that I’ve been wondering about.
When you’re viewing the CVD webpage, scroll down near the bottom to the “Design guides by category”…as you can see, there are a ton of options which should cover just about anything you are interested in.
Enjoy!!
CRON, CRONTAB, and Cobwebs
I found myself today working on my main SYSLOG server, which runs Linux (CentOS to be exact). I needed to change some startup scripts and update my CRONTAB entries. Note…CRONTAB is the process which will automatically run commands and scripts whenever you want it to…it can handle a lot of work when you are not around.
However, it has been a long time since I last worked with CRON and CRONTAB, and I needed to clear out some old cobwebs in the brain and refresh my memory on how all of this worked. I found a really good webpage that had some great explanations and examples for CRON and CRONTAB, and I was able to quickly get my changes completed and tested.
Check it out when you have a chance: https://www.pantz.org/software/cron/croninfo.html
And remember, if you need to test your SYSLOG server, check out SYSLOGGEN.
Enjoy!
Meraki Wireless – Basics and Best Practices
I’ve just recently completed an enterprise wide wireless upgrade to Meraki AP’s. I have to say it brought joy to my heart to get rid of all those old (very old!!) Cisco AP’s. Wow…they were such boat anchors! Now we have a state of the art, cloud managed, wireless infrastructure that will support my company for many years to come. And management is SO much easier now…all from a single pane of glass. To be honest, I’m not a huge preacher for “cloud” management solutions…but for a wireless network, Meraki’s cloud management interface is incredible!!
To get you started, you should check this out: Meraki Wireless Basics and Best Practices
Make sure to click on all three tabs…Guides, Articles and Most Popular. Lots of great information, and a fair of amount of it pertains to generic wireless networks, not just Meraki.
Enjoy!