I had an issue come up today in which I needed to verify what mail servers were handling email for a particular domain. (I like having easy problems on a Friday!)
So, how do you answer this question? Simple…you need to look up the MX records associated with the domain in question. MX stands for Mail Exchange…which are DNS records of mail servers sitting on the Internet which handle email for a domain. Quick example using my handy DIG utility (available within Linux, or you can download it from isc.org for Windows)…
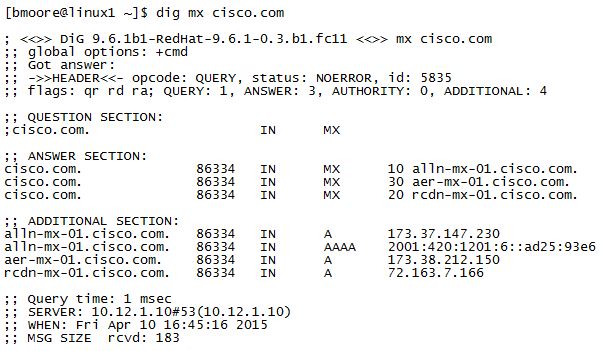
MX results for cisco.com
As you can see, the DNS reply gave us 3 MX records for mail servers that handle email for the domain “cisco.com”…
10 alln-mx-01.cisco.com.
30 aer-mx-01.cisco.com.
20 rcdn-mx-01.cisco.com.
The numbers in front of each line are known as “preference numbers” and establish which order the servers are to be used, with the smaller number being more preferred. In this case, mail servers will attempt to contact server alln-mx-01.cisco.com first, and if not successful, will then attempt server rcdn-mx-01.cisco.com….and so on. (And no, Cisco does not have a single server that takes care of all their email…most likely alln-mx-01 simply points to a large server cluster). A common technique you will see is to list several servers all with the same preference number…this allows for load-balancing among the servers (a bit crude, but it does work). HP handles load-balancing a bit differently…
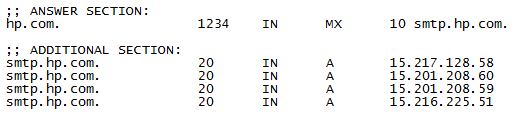
MX results for hp.com
I like HP’s solution…simple and efficient…there is only one MX record, but multiple “A” (Address) records that smtp.hp.com resolves to. How about Apple?….
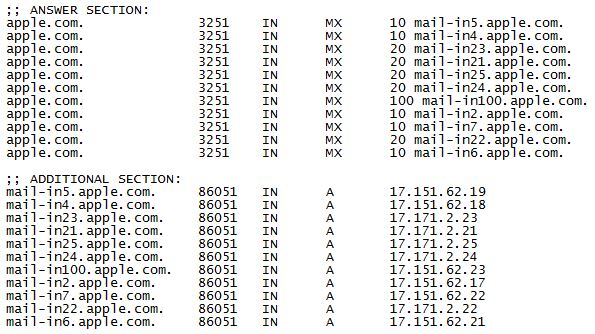
MX results for apple.com
As you can see, Apple handles load-balancing in a bit more complex manner, but it works very well…(sounds just like Apple, doesn’t it?). There are 5 preference number “10” servers and 5 “20” servers, and I bet they are spread out all over the place…different data centers in America and perhaps other parts of the world. Notice the single “100” preference server, which will only get used if none of the other servers are up and running. Knowing Apple, I’m sure this server is kept up to date and patched. But smaller organizations tend to setup a high number preference server as a last backup, which hardly ever gets used, and they tend to forget about it…maybe not keep up with patches and security updates. As a result, you will tend to see hackers go after the high numbered preference mail servers, as they may be an easier target.
Bonus question: Did you notice that all the host names and domain names ended with a “dot”, such as apple.com. and smtp.hp.com.? Know why? I’ll tell you in my next blog.
Hope this info was helpful…