My home PC is over 7 years old, and let me tell you…it was past time for an upgrade. I’ve been running Photoshop and Lightroom, along with an old version of VMware Workstation…talk about old and s-l-o-w! I started planning for a new PC earlier this year, but wasn’t really in a rush…just sort of waiting for something to push me over the edge…the “time to buy” edge.
Well, that edge was Cisco VIRL (Virtual Internet Routing Lab). One of the classes I attended at this years CiscoLive in San Diego concerned Cisco’s efforts in virtual network simulation. They have a commercial product (CMD – Cisco Modeling Labs), and they have a personal edition (VIRL). CMD is very expensive…as in, well…VERY. However, VIRL is reasonably priced…$200/year (it’s subscription based). VIRL is incredibly powerful and flexible; you can design and run many different types of simulated networks, all running real Cisco IOS (IOSv actually…a virtualized version of IOS). There is a limit of 15 nodes though…yes, that’s not really enough, but it does let you do a lot of testing and learning. (Visit here for more info on VIRL.)
Back to my PC. There was NO way it would ever be able to run VIRL…so I just had to buy a new one. 🙂
As you can tell, I don’t buy new PC’s often, so I wanted to make sure they last. The specs on my new PC…
- Intel i7 Quad-core processor (3.6 Ghz)
- 32 GB of RAM (VIRL loves RAM!!)
- Nvidia Graphics card with 4 GB RAM
- 1 TB hard drive
- 256 GB Samsung 850 PRO SSD drive (I added this in myself)
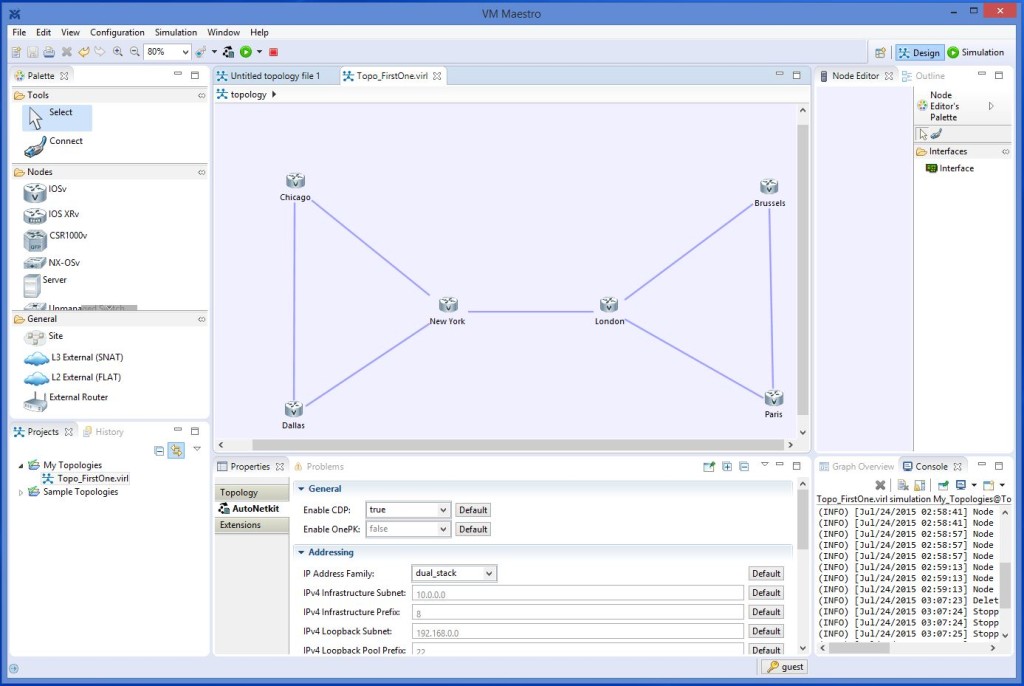
Wow…let me tell you…this thing rocks! And I spent today installing and running VIRL. (This is not an easy installation…you really need to follow directions, but it’s not really that difficult. Knowing your way around Linux sure helps though.) Here is a screen shot of VIRL with 6 routers configured…
I have just scratched the surface of VIRL…it is incredibly complex, but that’s ok…I have a lot to learn, but the rewards will be well worth it. I will post more about VIRL soon.